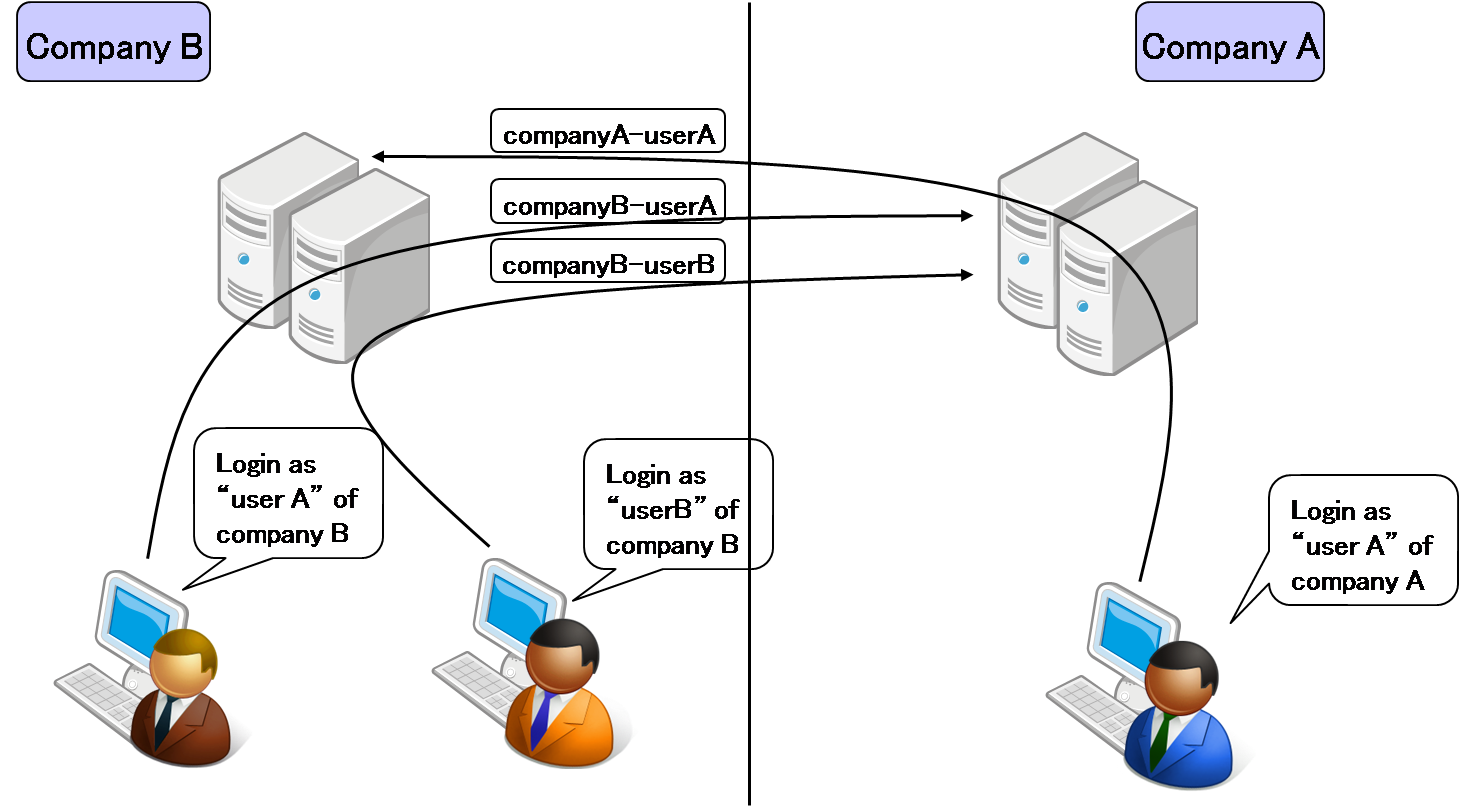
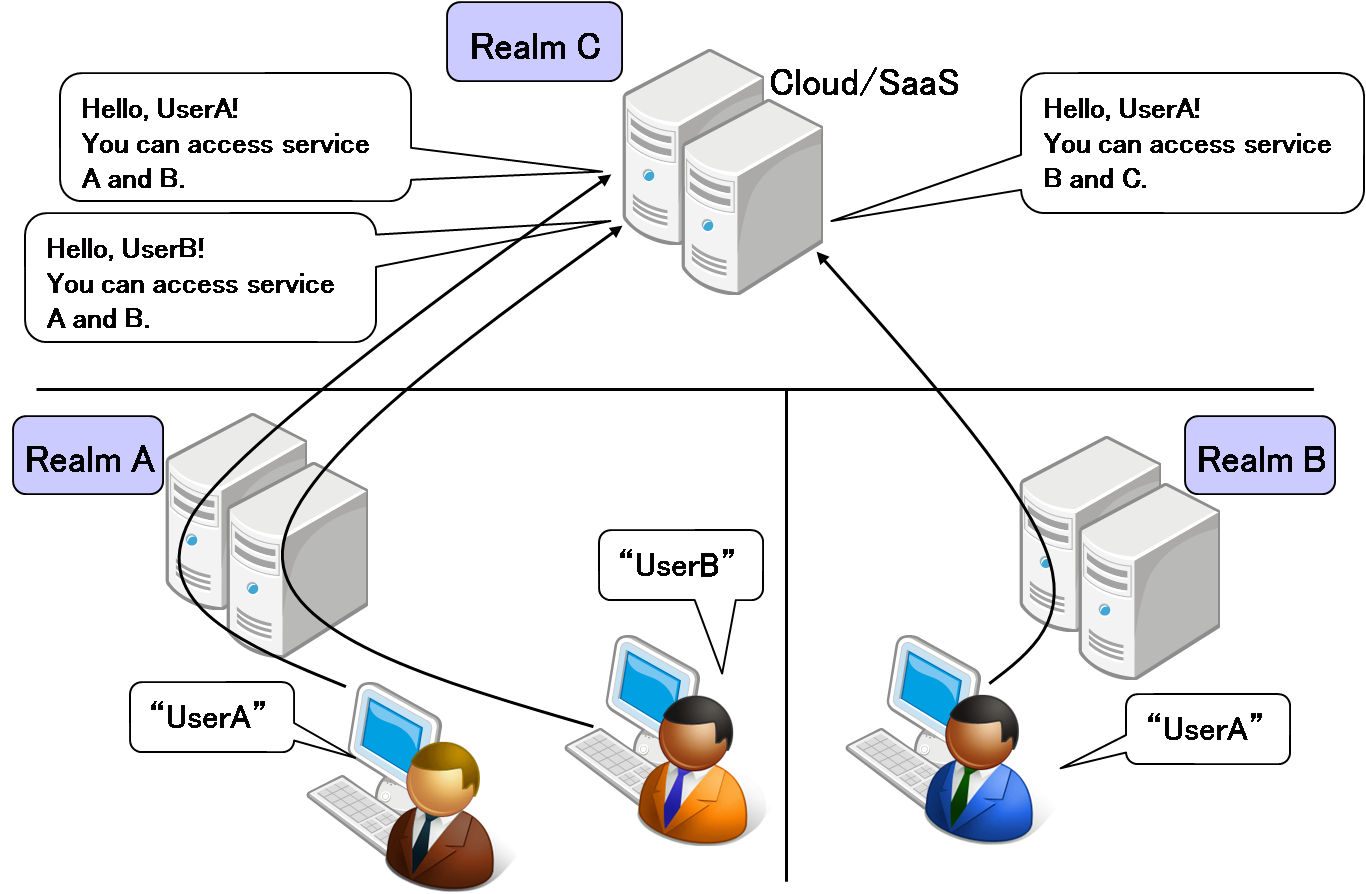
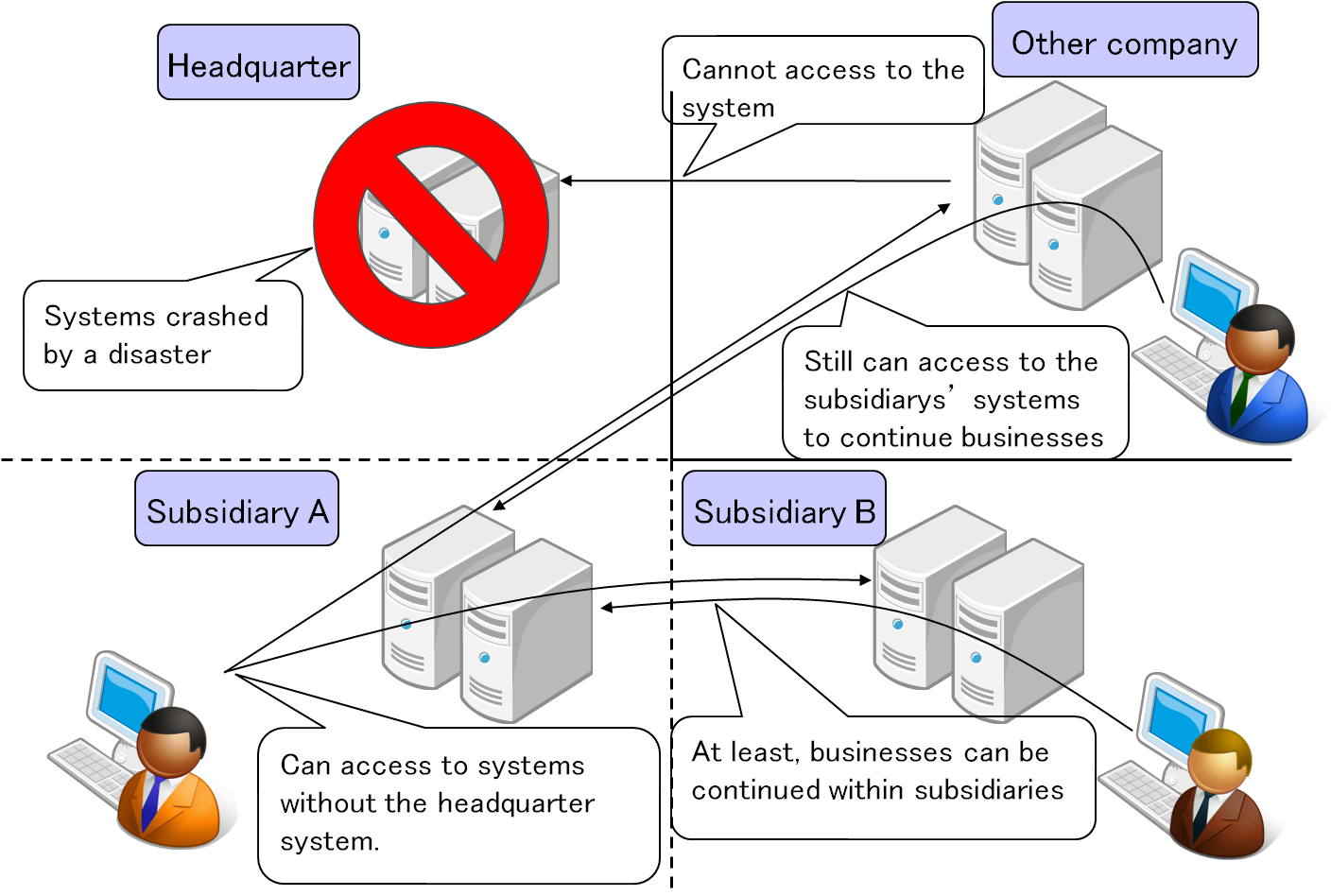
B to C (user attributes exchange)
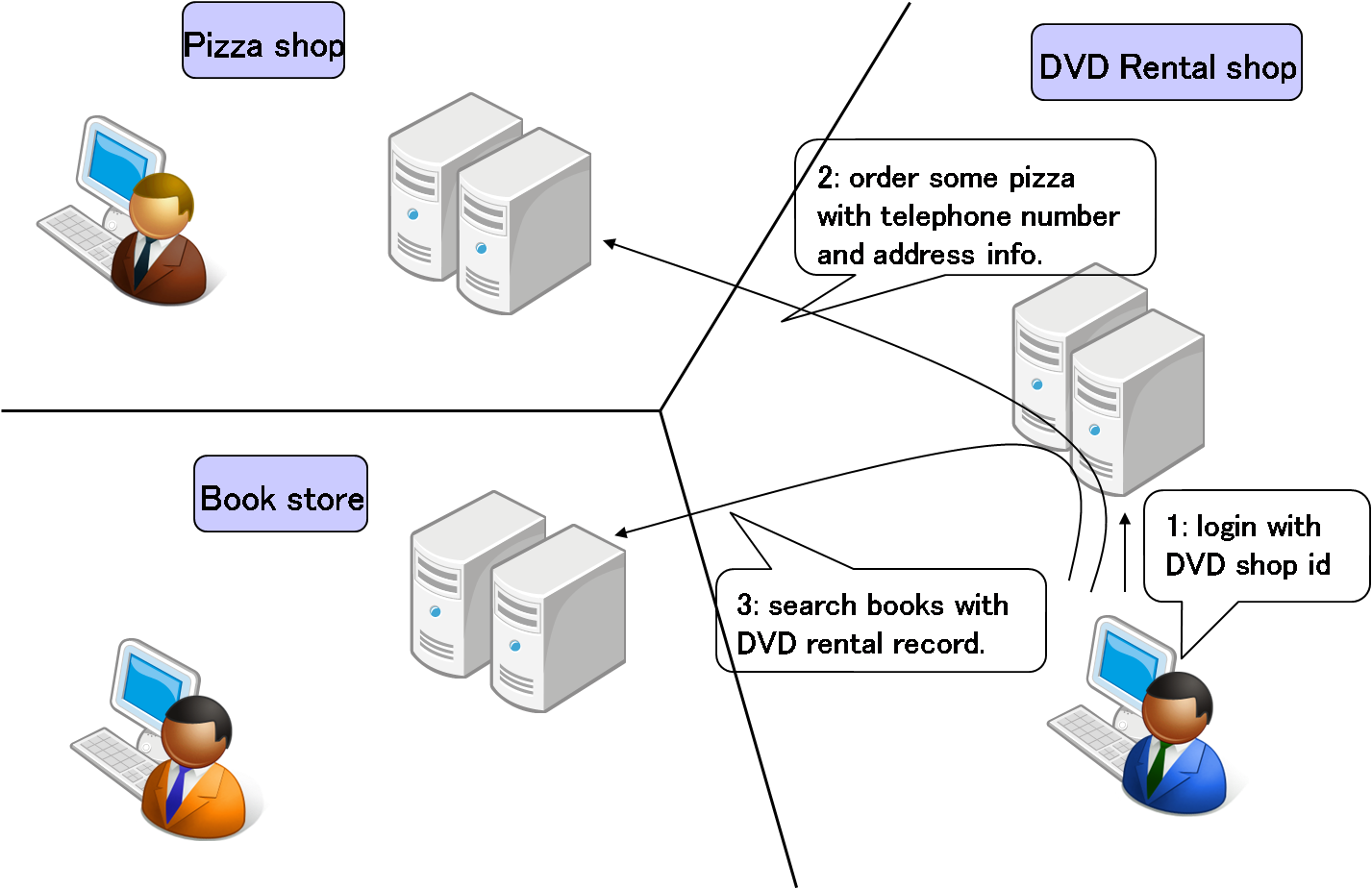
Let's say a user is registered in an online DVD rental store. 3 web sites, this DVD rental store, a pizza dilevery store and an online book store, are already configured with Eunomia mechanism.
The user accesses the pizza delivery store 's website to order a pizza after renting a DVD at the online DVD rental store. The DVD rental store sends the uid, telephone number and address information of the user to the pizza site according to the requests received.
After that, the user accesses the online book store to buy a book, so the DVD rental store sends the uid and a DVD rental history of the user so the online book store can create a customized recommendation list for the user.
In this case, the user's information is registered neither in the pizza store nor in the book store. Yet, the user experience is just like as if the user's information was stored in all the above mentioned websites. Adding servers and services can easily be done at each site, because the only thing that needs to be done is to configure the Eunomia mechanism of the new server with the public keys of other sites.